Automating Cloud Compliance Checks with Best Practices in AWS, Azure and GCP

Automating Cloud Compliance Checks with Best Practices in AWS, Azure and GCP
TLDR
- Managing multi-cloud compliance (AWS, Azure, GCP) is complex; manual checks are increasingly insufficient.
- Use built-in cloud tools (e.g., AWS Config, Azure Policy, GCP SCC) for automated compliance checks, providing ongoing validation and lowered risk.
- Automation significantly cuts data breach costs (average savings USD 1.88M) and speeds incident response (~100 days faster).
- Focus initial automation on foundational controls (encryption, access, logging) and expand strategically.
Managing cloud compliance has never been straightforward, especially when you’re working across multiple platforms and regulatory frameworks. From ISO 27001 and PCI DSS to HIPAA and SOC 2, the list of standards continues to grow, along with the complexity of staying aligned.
Rather than relying on point-in-time audits or spreadsheets to track control coverage, many teams are moving towards automation. The goal isn’t just to tick boxes. It’s to create a secure baseline that’s continuously validated, freeing up time and reducing risk.
This post looks at how AWS, Azure and GCP support automated compliance checks through native tooling, and how those capabilities can support a practical, risk-based approach to cloud security.
Why Automated Compliance Checks Matter
Manual checks often rely on documentation, tribal knowledge or last-minute audits. They’re inconsistent by nature, and gaps tend to be discovered after the fact. In contrast, automated compliance checks provide continuous assurance and help spot drift early.
When implemented well, automation:
- Reduces reliance on reactive audits
- Surfaces (and ideally remediates) misconfigurations as they happen
- Helps maintain alignment with known-good standards
- Supports audit readiness without repeated effort
Furthermore, adopting security AI and automation is proven to reduce these impacts significantly. The 2024 Cost of a Data Breach Report found that organisations using these technologies extensively lowered their average breach costs by USD 1.88 million. They also identified and contained breaches nearly 100 days faster on average compared to organisations without significant AI and automation use[cite: 138].
From a risk perspective, enforcing the basics – encryption, access controls, logging – also allows security teams to focus on higher-value concerns like business logic and architecture-specific issues.
Frameworks and Standards Supported Across Clouds
Most major public cloud providers offer guidance and technical alignment with a common set of standards, including:
- ISO/IEC 27001
- PCI DSS
- HIPAA
- SOC 2
- GDPR
- FedRAMP
- CIS Benchmarks
- NIST 800-53
The level of integration varies, but all three platforms offer a combination of documentation, managed policies, dashboards and API support to help map cloud configurations to these requirements.
AWS: Config Rules, Security Hub and Automated Remediation
AWS provides a strong set of tools to build automated compliance into your environment.
AWS Config lets you define rules to evaluate resources against specific criteria. These can be AWS-managed or custom rules tailored to your needs. If a resource fails a check, it can trigger automatic remediation through Lambda functions.
AWS Security Hub brings findings together into a single view and includes built-in standards like the CIS AWS Foundations Benchmark. It integrates with Config, GuardDuty and other services to give an overall view of security posture.
Audit Manager can help map technical findings directly to compliance frameworks, which is useful for teams preparing for formal assessments.
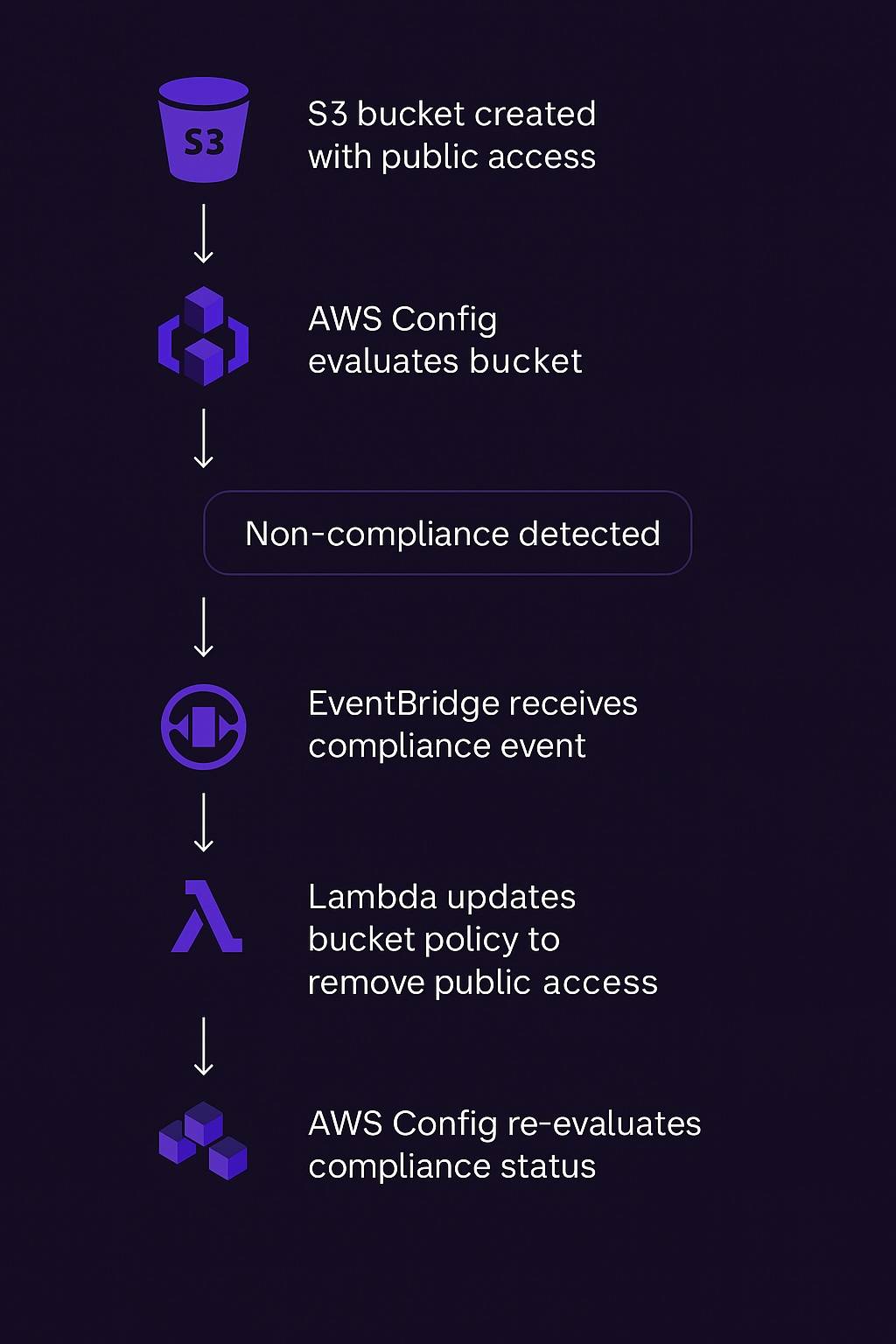
Let’s look at an example based on the diagram below (Fig. 1). If an S3 bucket is created with public access, an AWS Config rule detects it. Amazon EventBridge receives the compliance event and triggers an AWS Lambda function, which then auto-remediates by applying a secure bucket policy.
This entire detection and correction process occurs without manual intervention.
Azure: Policy-as-Code and Defender for Cloud
Azure’s compliance features are built around policy enforcement and visibility. With Azure Policy, you can define and assign policy definitions to enforce configuration standards across subscriptions or management groups. Built-in initiatives support standards like ISO 27001, NIST and CIS.
Microsoft Defender for Cloud, a cloud-native application protection platform (CNAPP), adds monitoring, recommendations and scoring based on your current setup. It integrates directly with Azure Policy and can highlight areas that fall outside of your defined compliance goals.
Secure Score offers a prioritised view of issues and opportunities to improve security posture, and Microsoft Sentinel offers advanced security monitoring, threat detection, and response capabilities using collected logs and signals.
If, for example, a developer tries to deploy an Azure storage account (a container for data services like Blob storage) without encryption, Azure Policy can block the deployment outright, or allow it while flagging it as non-compliant, depending on your enforcement mode.
GCP: Asset Inventory and Custom Policy Enforcement
Google Cloud offers several tools for monitoring compliance, although it leans more towards flexibility than pre-packaged frameworks.
Cloud Asset Inventory helps track all deployed resources across an organisation. This visibility forms the foundation for monitoring and auditing.
Security Command Center (SCC) brings together findings from different services and can include custom detectors to check for specific misconfigurations. For teams that want more control, Forseti Security – an open-source tool – allows for custom policy definitions and scanning, complementing GCP’s evolving native tools like Organisation Policy Service and Policy Controller for policy-as-code enforcement.
An example use case might involve detecting overly permissive IAM roles across projects, triggering an SCC alert, and flagging it for remediation or policy adjustment.
How Automation Helps You Stay Focused on Real Risks
Automated compliance checks do more than meet audit requirements. They help ensure your cloud environment stays aligned with key controls like encryption, logging, and access management.
By catching misconfigurations early and enforcing standards automatically, teams reduce manual effort and gain space to focus on higher-value work, whether that’s improving deployment speed, responding to incidents, or analysing risks to critical assets.
Consistent guardrails also make it easier to manage security at scale without relying on manual checks or tribal knowledge.
Start Small, Scale Sensibly
You don’t need to automate everything straight away. A good starting point is the basics: encryption, identity management, public access restrictions and logging. Use built-in frameworks like the CIS Benchmarks to bootstrap your rules, then adjust them based on your architecture and risk tolerance.
Over time, integrate compliance checks into your deployment pipelines, and move from alerting to remediation where it makes sense.
What matters most is that your compliance controls aren’t sitting on paper — they’re enforced, measured and improving as your environment grows.