Threat Modeling with Attack Trees
Threat Modeling with Attack Trees - A Practical Introduction
TLDR
- Threat modeling aims to identify, understand, and prioritise potential security threats to your systems.
- It helps security teams focus their efforts where they matter most.
- Attack trees offer a straightforward visualisation technique that makes this process more structured and easier to communicate.
What Are Attack Trees?
Attack trees provide a way to map out the various paths an attacker might take to achieve a specific goal. The structure is simple:
- The root node represents the attacker’s ultimate objective
- Branches show different attack methods
- Leaf nodes represent specific actions an attacker might take
Think of an attack tree as a roadmap of potential attacks - it visualises possible routes to a successful breach.
Building Attack Trees: A Practical Example
Let’s walk through how to build an attack tree using a common scenario: an attacker attempting to gain system access. It’s important to note that this simplified tree focuses specifically on obtaining credentials to gain access and doesn’t cover other methods like exploiting vulnerabilities directly. We keep it simple here to build intuition.
-
Define the ultimate goal: Start with the attacker’s objective at the top (root) of the tree - in this case, “Gain System Access”.
-
Identify key prerequisites: Determine what the attacker needs to achieve their goal - in this case, obtaining valid credentials is a critical first step.
-
Identify attack methods: Branch out into different approaches to achieve the credentials goal:
- Social Engineering
- Purchasing from Initial Access Brokers
- Exploiting Data Leaks
- Password Spraying
- Credential Stuffing
While shown as separate paths, it’s worth remembering that data leaks often provide the raw material for credential stuffing and can inform password spraying targets. The tree structure doesn’t explicitly show this dependency but represents them as distinct actions an attacker might take.
-
Add detail to each branch: Break down each method into specific actions.
Applying those steps, here’s the structure of our example attack tree focusing on obtaining credentials:
- Obtain Valid Credentials (Goal)
- Social Engineering
- Phishing/Vishing Attacks
- Purchase Credentials
- Buy from Initial Access Broker
- Data Leak Exploitation
- Utilise Leaked Credential Data
- Password Spraying
- Try Common Passwords Across Multiple Accounts
- Credential Stuffing
- Use Credentials from One Breach on Other Services
- Social Engineering
This example shows multiple ways to achieve the intermediate goal of obtaining credentials.
Using Attack Trees Effectively
Once you’ve built your attack trees they can be used as part of the wider threat modeling process. Areas for discussion include:
- Assess likelihood:
- Which paths are most likely to be used?
- Evaluate impact:
- Which successful attacks would cause the most damage?
- Rate difficulty:
- How hard is each attack method to execute? This often requires practical insights gained from real-world assessments, as attacker resources and techniques constantly evolve.
- Identify weak points:
- Look for areas where multiple attack paths converge or where defences seem weakest - these are high-priority protection points.
- Develop countermeasures:
- Based on the assessment, develop specific defences. In our consulting work, we prioritise countermeasures that offer the highest risk reduction for the specific client context.
While attack trees excel at visualising how specific attacks might unfold, this analysis in practice often integrates with broader methodologies like STRIDE (for threat categorisation), DREAD (for risk rating), or others, which inform the overall assessment.
For our credentials scenario, countermeasures resulting from this analysis could include examples like:
- Security awareness training (against social engineering)
- Multi-factor authentication (mitigates credential theft)
- Password breach monitoring
- Account lockout policies (against password spraying)
Enhancing Attack Trees with MITRE ATT&CK
The diagram below visualises the attack tree example we’ve been building. It lays out the discussed paths for obtaining credentials and incorporates the corresponding MITRE ATT&CK technique IDs for each method shown.
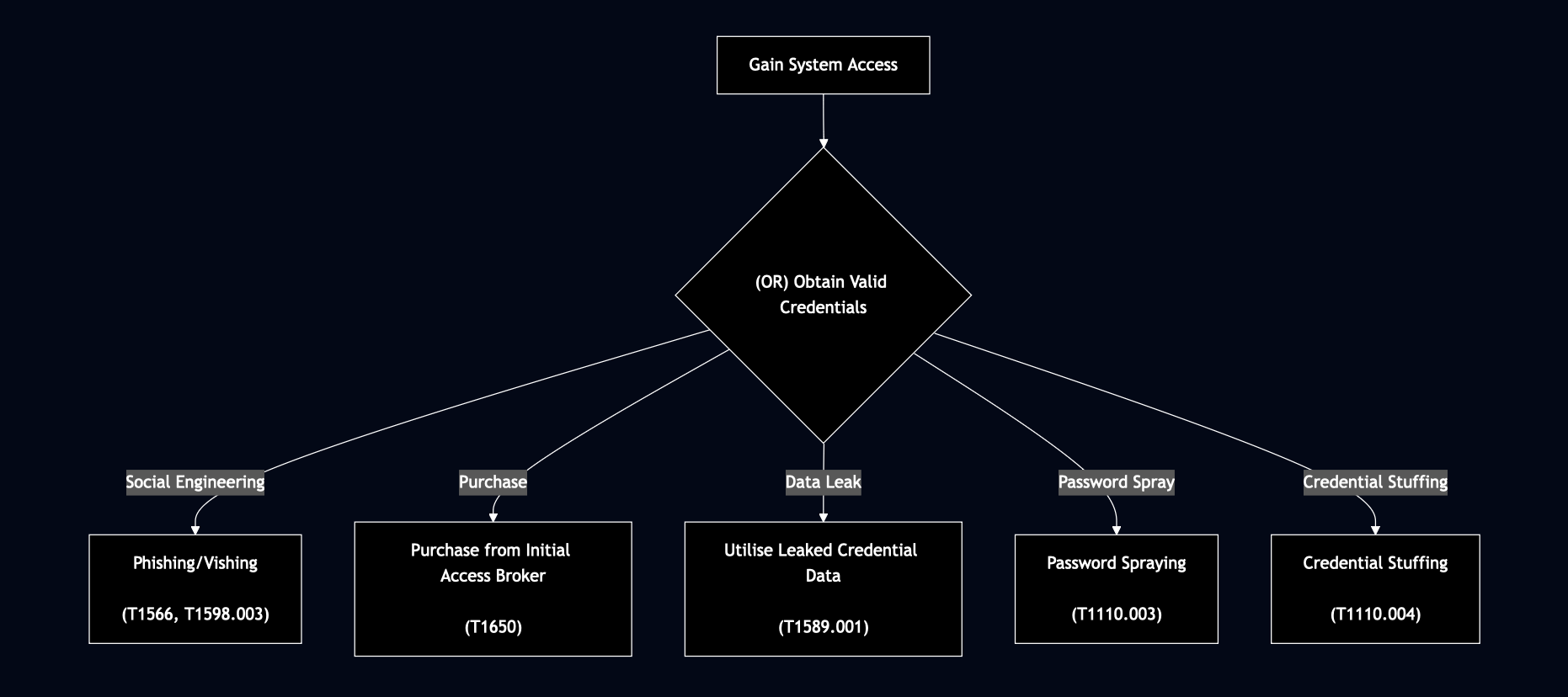
Attack trees can potentially become more useful when mapped to standardised frameworks like MITRE ATT&CK. By associating each attack vector with specific ATT&CK technique IDs:
- Security teams can link threats to specific, documented attack techniques
- Defenders can quickly identify relevant mitigations based on technique IDs
- The organisation builds a common language (ontology) for discussing threats
Using our credential theft example, we can map each branch to specific technique IDs:
- Social Engineering → Phishing/Vishing (T1566, T1598.003)
- Purchase → Purchase from Initial Access Broker (T1650)
- Data Leak → Utilise Leaked Credential Data (T1589.001)
- Password Spray → Password Spraying (T1110.003)
- Credential Stuffing → Credential Stuffing (T1110.004)
This mapping provides security teams with a wealth of additional info about each attack technique, typical adversary groups that use them, and recommended mitigations - all through the standard MITRE ATT&CK knowledge base. These mappings are just initial examples. Others exist and can likewise be mapped.
Expanding the Attack Tree: Beyond Initial Credentials
Our simplified tree mapped routes to obtain credentials, but a real-world attack often proceeds to more complex stages. We should now iterate and look at what happens next, particularly when Multi-Factor Authentication (MFA) stands in the way (e.g., service lacks MFA, unenforced MFA, or user not enrolled, among others). The specific additional areas covered would depend on the scope of the engagement.
Conclusion
Attack trees help bring clarity and structure to threat modeling by breaking down complex attacks into their component parts. They’re not meant to be the only tool you use, but rather a practical way to visualise and communicate specific attack scenarios.
Start simple with your most critical assets, build trees for the most likely attack goals, and use what you learn to strengthen your overall security posture. The power of attack trees lies in their simplicity - they take complex security concepts and make them accessible to everyone involved in protecting your systems.
For organisations looking to implement a comprehensive threat modeling program, our professional threat modeling services can help establish systematic approaches to security risk identification and mitigation.
For more information on threat modeling fundamentals, explore our comprehensive FAQ covering methodologies, implementation strategies, and common challenges.