Zero Trust Maturity Model: Assessing Identity Maturity
Introduction: Why Identity is Key in Zero Trust
In the Zero Trust security model, identity is often described as the new perimeter. This signifies a fundamental shift: rather than trusting based on network location, the model aims to verify every access attempt, operating on the principle that threats can originate from anywhere. Identity is central to making this work. It’s not just about user accounts. It includes devices, applications, and services. Anything that needs access.
If you’re short on resources, focusing on strong identity verification and access control (MFA, role-based access, SSO) is usually the highest-impact first move.
To help organisations implement Zero Trust, the US Cybersecurity & Infrastructure Security Agency (CISA) developed a Zero Trust Maturity Model. This model breaks down the complex topic into five core pillars, including Identity, which is the focus of this post.
Within each pillar, CISA outlines key capability areas they call Functions, described across four maturity stages: Traditional, Initial, Advanced, and Optimal.
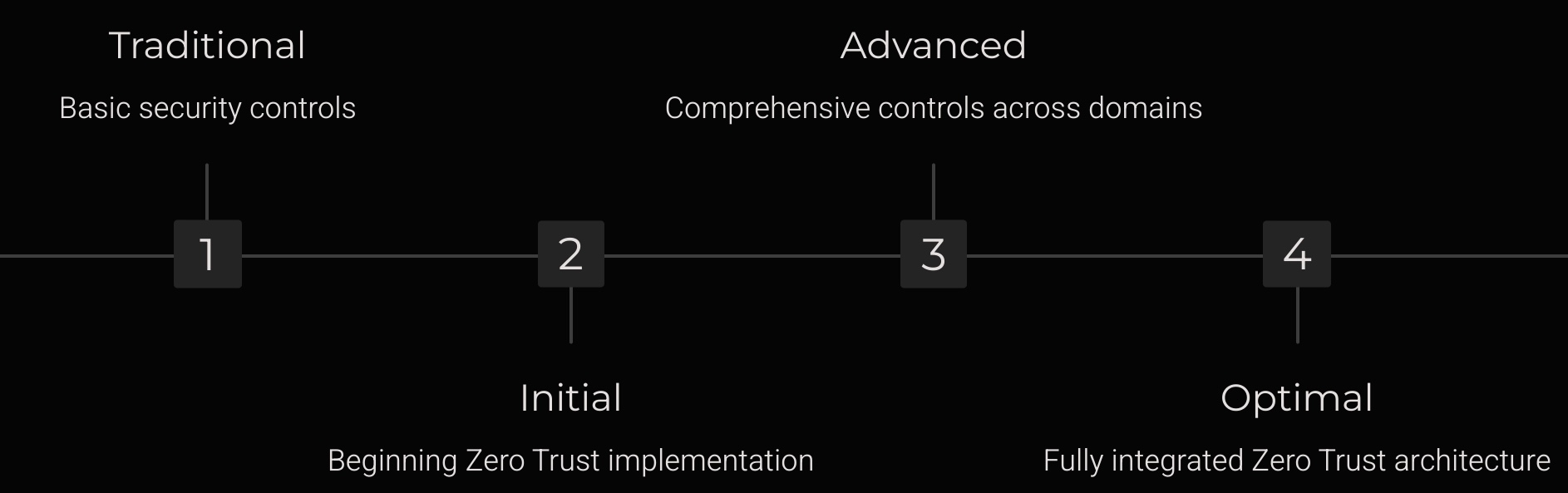
How We Break It Down
This post uses the CISA Zero Trust Maturity Model to explore the Identity pillar’s key functions. Rather than treating the model as a set of strict rules, think of it as a way to understand what “better” looks like. We walk through each maturity level and highlight why these functions matter, helping you start thinking about where your organisation stands today.
Strengthening Identity Verification and Authentication
The principle ‘never trust, always verify’ means Zero Trust starts by verifying an entity’s claimed identity. Passwords alone don’t cut it anymore against modern threats like phishing, and even basic MFA can be bypassed using sophisticated techniques like infostealer malware. Zero Trust requires stronger proof, highlighting the importance of progressing through the CISA maturity levels for authentication.
Understanding CISA’s Authentication Maturity Levels
Let’s look at what each stage of maturity means for the Authentication function according to the CISA model:
- Traditional: Identity authentication relies on either basic passwords or multi-factor authentication (MFA), often inconsistently applied. Access for entity identities (like service accounts) is typically static.
- Initial: You’re likely using multi-factor authentication (MFA), but passwords might still be one of those factors. You check other attributes like location or recent activity to help validate the login.
- Advanced: You start requiring phishing-resistant MFA for all identities. This means beginning to roll out passwordless methods like FIDO2 security keys or potentially certificate-based options.
- Optimal: Strong, phishing-resistant MFA isn’t just for login; identity is validated continuously throughout a session. Access can be adjusted on the fly if risks change.
Context and Consequences: Authentication Failures
Weak authentication methods are increasingly exploited. Data from the Check Point 2025 Cyber Security Report showed that Infostealer attacks, designed to steal credentials and session cookies (which can bypass MFA), saw a 58% increase in attempts affecting organizations in 2024.
This directly challenges Traditional/Initial maturity levels and underscores the need for Advanced (phishing-resistant MFA) and Optimal (continuous validation) controls to mitigate credential theft and session hijacking.
Threat Context:
Securing and Integrating Identity Stores
Most organisations have identity information scattered across different systems – old on-premises directories, cloud services, application-specific databases. Zero Trust works best when these are securely consolidated and integrated.
Understanding the CISA Stages for Identity Store Management
- Traditional: The organisation primarily uses self-managed, on-premises identity stores.
- Initial: You have a mix of self-managed (e.g., on-premises directories) and hosted (e.g., cloud) identity stores. Integration is probably minimal, maybe just some basic single sign-on (SSO).
- Advanced: You actively start to securely consolidate and integrate these different identity stores, aiming for a more unified system.
- Optimal: Your identity stores are securely integrated where needed, including with partners (e.g., via federation or managed external accounts). Identity management is consistent, possibly automated, and might be linked to authoritative sources like an HR system.
The Importance of Secure Identity Stores
Managing identities across hybrid environments introduces significant risk if not done securely. Data from the Check Point 2025 Cyber Security Report revealed that hybrid environments integrating on-premise resources with cloud services via IAM providers have become prime targets, enabling attackers to move laterally between cloud and on-premise systems.
Threat Context:
Assessing Identity Risk Dynamically
Recognizing that not all access attempts carry the same level of risk, Zero Trust necessitates analyzing signals in real-time to identify potentially compromised accounts or flag unusual behaviour before granting or continuing access.
CISA’s Maturity Levels for Identity Risk Assessment Explained
- Traditional: Only limited determinations of identity risk (the likelihood an identity is compromised) are made.
- Initial: You determine identity risk mainly through manual checks and static rules, giving you some basic visibility.
- Advanced: You start using automated analysis and dynamic rules to assess risk. This assessment directly influences access decisions and triggers security responses.
- Optimal: Identity risk is assessed in real-time using ongoing analysis, including behaviour patterns and dynamic rules, providing continuous, adaptive protection.
Why Assess Identity Risk Dynamically?
Understanding identity risk includes guarding against sophisticated insider threats. Data from the CrowdStrike 2025 Global Threat Report showed DPRK-nexus group FAMOUS CHOLLIMA conducted over 300 incidents in 2024, nearly 40% involving malicious insider threat operations where operatives obtained jobs within target companies.
Threat Context:

Governing Access with Least Privilege
A core Zero Trust principle guiding access management is ‘least privilege’ – give only the permissions needed to do a job, for the shortest time necessary. Just-in-time access provisioning with granular scoped role-based access controls (RBAC) and regular reviews.
Achieving Least Privilege: CISA’s Access Management Stages
- Traditional: Access (for both standard and privileged accounts) is typically granted permanently, relying on periodic reviews to revoke it.
- Initial: Access rights (especially for privileged accounts) expire after a set time and undergo automated reviews.
- Advanced: Access becomes more fine-grained, based on need within a specific session. Privileged access is tailored to specific actions and resources.
- Optimal: Automation enables “just-in-time” and “just-enough” access. Permissions are granted precisely when needed, for specific tasks, minimising the risk from standing privileges.
Access Management: Mitigating Privilege Escalation
Failing to enforce least privilege significantly increases risk. Data from the Palo Alto Unit 42 Global Incident Response Report 2025 showed that in 41% of incidents, overly permissive accounts or roles were a contributing factor, allowing attackers to escalate privileges and move laterally far more easily than they should have.
Threat Context:

Enhancing Identity Operations: Visibility, Automation, and Governance
While CISA defines Visibility & Analytics, Automation & Orchestration, and Governance as foundational “Cross-Cutting Capabilities” applicable across all Zero Trust pillars, improving them is a key step for maturing identity security operations.
CISA’s Maturity Stages for Identity Visibility, Automation & Governance
- Traditional: Limited user/entity activity logs are collected (especially for privileged accounts) with some routine manual analysis. Identity orchestration (onboarding/offboarding) is manual with little integration. Policies are enforced via static technical means and manual review.
- Initial: Visibility comes from manual log reviews with limited ability to connect the dots. Automation might cover basic user account creation/deletion, but privileged/external accounts are handled manually. Policies exist but rely on manual checks or basic technical enforcement.
- Advanced: Log analysis becomes more automated, improving visibility across different systems. Most identity processes (provisioning, deprovisioning) are automated and integrated across environments. Policies are enforced more consistently through automation and updated regularly.
- Optimal: You have comprehensive, real-time visibility through advanced, automated analytics (including behaviour). All identity orchestration is fully automated, integrated, and adapts dynamically. Policies are also fully automated, continuously enforced, and updated dynamically across all systems.
Why Focus on Visibility, Automation & Governance?
Investing in automation and analytics for security operations yields significant returns. Data from the IBM Cost of a Data Breach Report 2024 showed that extensive use of security AI and automation significantly reduces breach costs (by an average of USD 2.2 million in prevention workflows) and speeds up response times (by nearly 100 days on average).
Threat Context:

Conclusion: Taking the Next Steps with Identity
Improving your organisation’s approach to identity is fundamental for Zero Trust. By understanding and working on the key capability areas – the Functions defined by CISA – and assessing your position across the Traditional, Initial, Advanced, and Optimal stages, you can build a much stronger security foundation.
Look at where your organisation stands today across Authentication, Identity Stores, Risk Assessment, Access Management, and the supporting operations. Focus on practical steps like adopting phishing-resistant MFA, unifying identity management where possible, using risk signals to inform decisions, enforcing least privilege, and automating consistently. Consider getting a professional assessment to understand your current maturity. It’s an ongoing process, but these steps move you towards a more secure, identity-aware environment.