Zero Trust: What It Is and Why It Matters

Zero Trust: What It Is and Why It Matters
TLDR
- Complex threats, combined with widespread cloud/IoT adoption and remote work, have made traditional perimeter security insufficient, driving the need for Zero Trust.
- Implementing Zero Trust aids compliance with standards and regulations like ISO 27001, FedRAMP, HIPAA, and PCI DSS by embedding strict verification and least privilege.
- Zero Trust operates on the principle: Never Trust, Always Verify.
- The CISA Zero Trust Maturity Model offers a structured path (Traditional to Optimal) based on 5 pillars (Identity, Devices, Networks, Applications, Data) and 3 capabilities (Visibility, Automation, Governance).
This initial overview covers why it’s needed and its core (“Never Trust, Always Verify”). We’ll dive deep into the 5 pillars (Identity, etc.) in future posts.
Here is the first one on the Zero Trust Identity pillar
The Shift from Perimeter Security
For years, IT security followed the ‘castle-and-moat’ strategy: build strong external walls to keep threats out. But as cyber threats evolved and IT environments grew vastly more complex, this perimeter-focused model started showing cracks. Zero Trust offers a fundamental shift in perspective, built on the core idea that trust should never be implicit. Instead, verification must be continuous.
Why Zero Trust? The Driving Forces
The move towards Zero Trust isn’t arbitrary; it’s a response to significant changes in how businesses operate and the threats they face:
- Evolving Threat Landscape: Sophisticated attacks like ransomware, insider threats, and supply chain compromises often bypass traditional defences. Zero Trust demands internal vigilance, assuming threats might already be inside.
- Enabling Digital Transformation: Today’s businesses run on interconnected ecosystems spanning clouds, APIs, IoT devices, and SaaS applications. This dissolves traditional network boundaries, requiring security that verifies access everywhere, not just at the edge.
- Supporting Secure Workforce Mobility: The rise of remote and hybrid work means users and devices connect from anywhere. Zero Trust securely enables this flexibility by constantly verifying user identities and device health, regardless of location.
- Complexity of Modern Environments: Today’s hybrid and multi-cloud setups render traditional perimeter-based security inadequate. Zero Trust addresses this by applying security controls directly to resources and users, regardless of where they are located

Zero Trust and Regulatory Alignment: Building Trust Through Verification
Adopting a Zero Trust architecture provides more than just enhanced security; it significantly helps organisations meet strict compliance requirements like those found in ISO 27001, FedRAMP, HIPAA, and PCI DSS.
By inherently enforcing principles such as least privilege access and rigorous verification, Zero Trust demonstrates a proactive commitment to data protection and privacy. This can help avoid regulatory fines and build confidence among stakeholders that security is a core strategic priority.
Navigating Implementation: The CISA Zero Trust Maturity Model
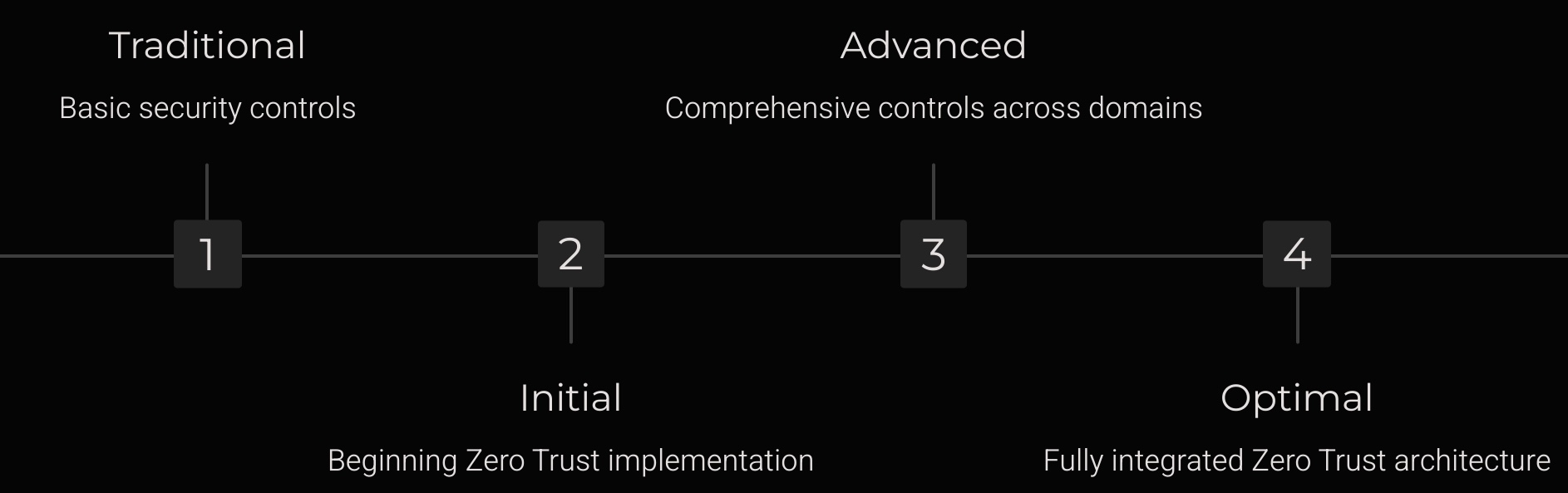
Developed by the US Cybersecurity and Infrastructure Security Agency (CISA), the Zero Trust Maturity Model offers a valuable guide for implementation.
While initially created with US federal agencies in mind, its principles and structure serve as an excellent framework for organisations globally, regardless of sector. It helps organisations assess their current capabilities and chart a clear, phased roadmap to progressively enhance their Zero Trust posture through defined maturity stages: Traditional, Initial, Advanced, and Optimal.
The Five Pillars and Supporting Capabilities
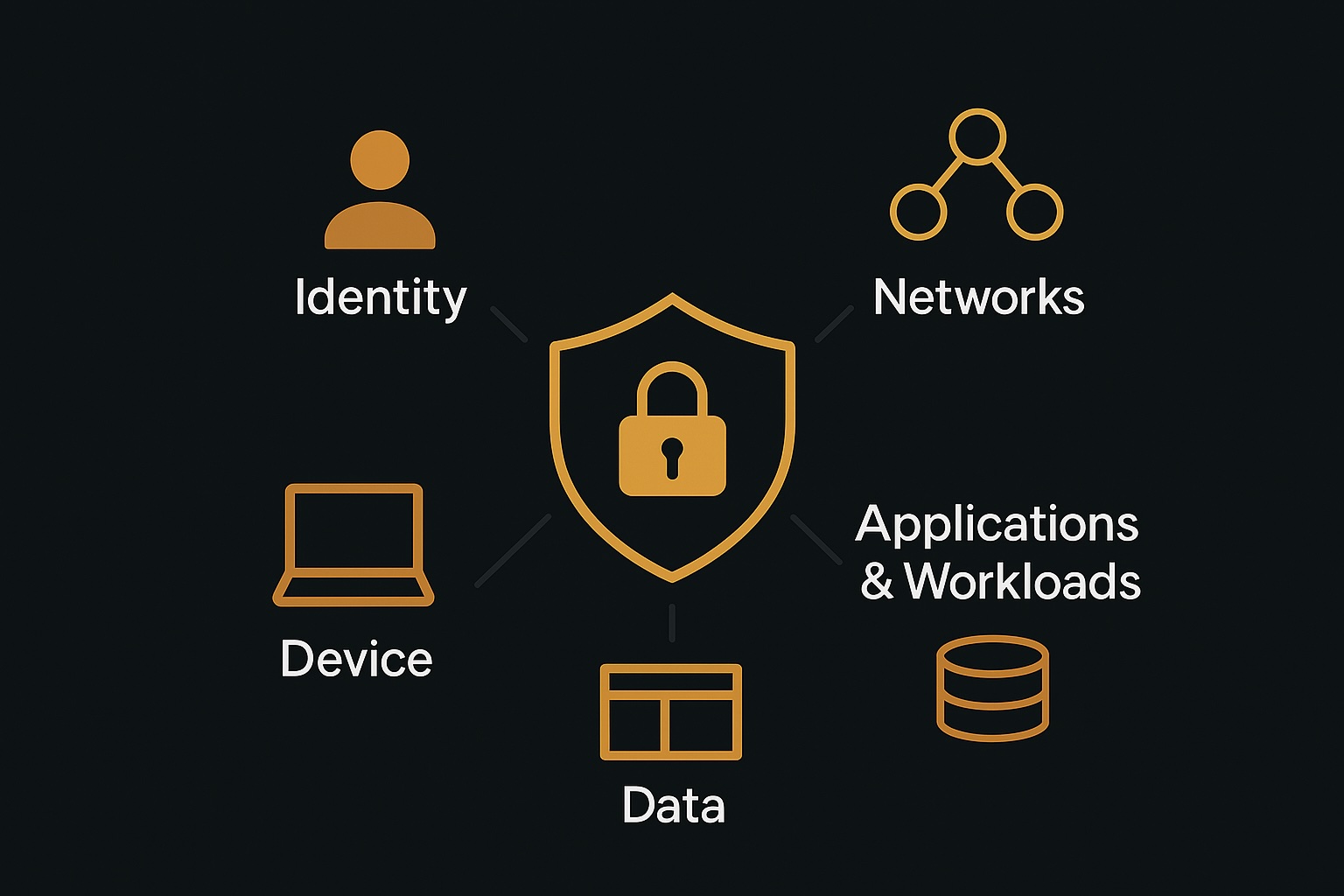
CISA structures this journey around five core pillars and three cross-cutting capabilities.
These core building blocks, as defined by the CISA model, are formally grouped into five central pillars focusing on specific security domains, alongside three cross-cutting capabilities that provide foundational support across the entire architecture.
The Five Pillars:
- Identity: Robustly authenticating and continuously verifying users.
- Devices: Continuously checking the health and compliance status of devices seeking access.
- Networks: Segmenting networks and managing access controls effectively (micro-segmentation).
- Applications & Workloads: Securing access to applications and ensuring secure interactions between workloads.
- Data: Protecting sensitive data through strong access controls, encryption, and classification.
Cross-Cutting Capabilities:
- Visibility & Analytics: Gaining comprehensive monitoring and insight across all pillars.
- Automation & Orchestration: Using automation to improve response times and consistency, reducing manual errors.
- Governance: Establishing policies and strategic oversight to align Zero Trust efforts with business objectives.
Together, these elements provide a holistic approach to building a mature Zero Trust environment step-by-step.
Vendor-Specific Guidance
Beyond the CISA model’s vendor-agnostic foundational framework, organisations implementing Zero Trust within specific cloud environments should also consult resources directly from their providers.
Vendors such as AWS, Microsoft Azure, and GCP offer detailed reference architectures, map their native security services to Zero Trust principles, and provide platform-specific guidance that complements the CISA approach. Microsoft even offers a detailed mapping to the CISA model with its Configure Microsoft cloud services for the CISA Zero Trust Maturity Model guide.
In the end, each Zero Trust journey will be highly contextual, shaped by the organisation’s existing technology investments, security maturity, compliance requirements, business objectives and available resources. By embracing this reality, security teams can craft a practical Zero Trust strategy that strengthens security posture without compromising operational efficiency or business innovation.

Looking Ahead
So, what’s the takeaway? Zero Trust principles are fundamental to navigating the complexities of modern IT, from digital transformation projects to securing a mobile workforce.
Don’t just treat it as a concept; use resources like the CISA maturity model to actively plan your implementation and prioritise based on continuous risk assessment, informed by threat modeling to determine where stricter verification and controls are needed most. Getting Zero Trust right means building security that can adapt and effectively defend against today’s (and tomorrow’s) attacks.
Stay tuned for further insights as we take a closer look at each of the CISA Zero Trust pillars in upcoming articles.